On the modern battlefield, the commander has access to an ever-growing volume of information from which to assess the situation and lead his command. He must quickly assimilate this information in order to influence the outcome of the operation; prioritize and allocate resources; assess and take risks; and understand the needs of higher and subordinate commanders. The commander depends upon a skilled G2 (S2) working within his intent to effectively direct and control his IEW effort. The ACE equipped with the ASAS is the G2’s (S2’s) primary organization for controlling IEW operations and producing intelligence.
| MISSION |
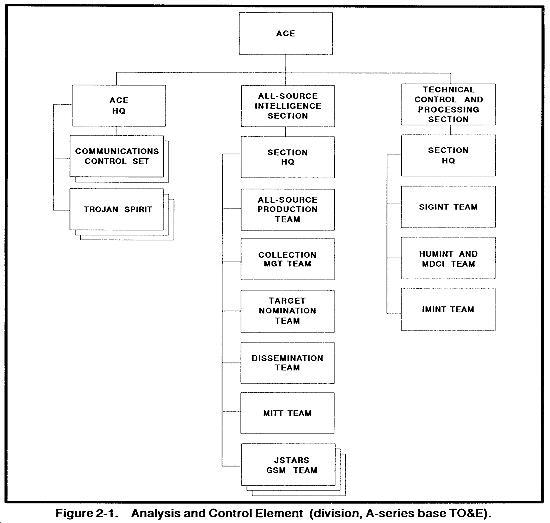
The mission of the ACE is to perform collection management; produce all-source intelligence; provide IEW technical control; and disseminate intelligence and targeting data. The ACE supports the commander in executing battle command and planning future missions across the range of military operations.
| ORGANIZATION |
The ACE integrates the missions, functions, and resources of the former technical control and analysis element (TCAE) and TOC support element (TOCSE) at corps, division, separate brigade, and ACR. At theater Army, the ACE replaces the Echelons Above Corps Intelligence Center (EACIC) and the TCAE. As the ACT, it replaces the IEW support element (IEWSE) and improves support at the divisional maneuver brigade. The ACE centralizes analysis and collection management in one organization under the operational control (OPCON) of the G2 (S2). The formation of the ACE goes beyond consolidation or collocation. The ACE provides balance to all-source analysis products and synergy to the execution of CI, human intelligence (HUMINT), IMINT, and SIGINT operations.
THEATER ARMY:
At theater Army, the ACE is organic to the operations battalion of the theater Army MI brigade. Under the direction of the theater Army G2, it works closely with the theater Joint Intelligence Center (JIC) to support the ground forces intelligence requirements of the theater Army commander and subordinates. The theater Army ACE is an integral element in IEW support to joint operations and the subordinate ground component. It supports the G2, and subordinate Army Force (ARFOR) by maintaining and deconflicting the theater’s databases on contingency area threat ground forces. The ACE, like the JIC, is an all-source intelligence center that gathers and disseminates intelligence in response to the commander’s requirements. In war or OOTW, the ACE complements the JIC and, with service component augmentation, can become the joint intelligence element of a joint task force (JTF). The common features of the ACE and JIC contribute to effective joint intelligence support of ARFOR units in war and OOTW.
See FM 34-37 and FM 100-7 for more information on theater Army IEW operations.
CORPS:
The corps ACE develops all-source intelligence needed to support corps contingency planning and operations. The ACE is organic to the operations battalion of the corps MI brigade although under the OPCON of the corps G2. The scope of corps ACE operations differs from those at lower echelons, although the basic process remains the same. The ACE links into a network of specialized single discipline intelligence collection assets and processors. The mix of these systems and access to joint intelligence activities are tailored to the specific demands of the operation and availability of resources.
~~~~~~~~~~~~~~~~~~~
So the time is here that we all knew was coming. Do you have an ACE set up in your area of operations? Do you have communications set up with protocols in place? Do you have ATAK software running at a base station?
There are reasons that I am posting the above information and questions. The first question that needs to be addressed is one of operational security. How do you know who is trustworthy? What is the level of trust: even a high level of trust can be compromised by blackmail and threats when the government is evil and not bound by the law.
I have two points for your consideration that were discussed this weekend:
- How do you evaluate trust and ensure the operational security of your community? We know what the government is capable of doing as the facts of the January 6th “insurrection” are now coming out. We know that the truth is not relevant as people sit in jail for misdemeanors in poor conditions. We know that no one is coming to save us.
- Trust has practical limitations. I may trust someone but that does not mean I have to give them information or intelligence that they do not need to know. I also take no offense if I am not given information or intelligence that I do not need to know. Operational security supersedes unnecessary information/intelligence transfers.
During one discussion concerning these points, I was asked of me what conditions would it take to “break” me or my trust. I replied that I understand that the evil we face is capable of anything. Why would I trust them to keep their word? How would the Lord judge me for colluding with evil? As General Flynn found out, they will threaten your family. If they are confident that they can coerce people by harming their loved ones, they will always put your loved ones in jeopardy even if you do cooperate. That is what evil does.
The short answer is that you cannot compromise with evil. Finding people who understand this is our greatest problem. Where to start? You must find what I call “true believers”: they understand what is at stake and their sacred Honor cannot be compromised.
I know this is a great task but you have to start at the beginning with a firm reliance on Divine Providence. Everything will revolve around your ACE. Information gathering, communications, operational security and the function of the ACE as outlined above are all necessary components to fighting evil. Trust in the Lord and pray for guidance.
David DeGerolamo




While very informative and accurate for gov.com operations. Local intelligence and MOST Important OPSEC as not to be betrayed (a CRITICAL Failure of Rebels) is far simpler.
Know whom you trust with your life and freedom. KNOW their families as the Weakest Link IS the WEAK LINK of the trust system. Protect your families from getting USED as a breaking tool against you and your peers.
Local, local, local. If you need meetings to discuss plans you already have too many vulnerable members OR Feds already inside your group.
Electronics are NOT your friend. Gov.com has way too many ways to tap into your “Secure Commo”. Electronic security is a matter of pure computer power.
WHO HAS THE SUPERCOMPUTERS? Nuff said.
I agree with your assessment. KISS principal.
Zones – Area Ocho
Training Manuals – Area Ocho
Well, while I understand the ramifications, I am basically on my own to receive the consequences of my actions. I have no one to fall back on. Good neighbors yes; but they are busy with their lives and hope everything will not affect them. Some folks are aware of what we face but are too busy with day-to-day activity. No one is able to form anything. Wait and see attitude. Yup, I’m on my own. Family scattered to the four winds. They are on their own. I can’t fight their war for them. They have their own take on everything. The old man is a paranoid nutcase. Yeah, well…. I have no problem dying. That’s in the cards for all of us…some sooner than others. Just pisses me off that the war won’t start. Hope I’m still around when it does. Getting long in the tooth.
Never Too Old – Area Ocho Me and you both Eddie.
Thank you.