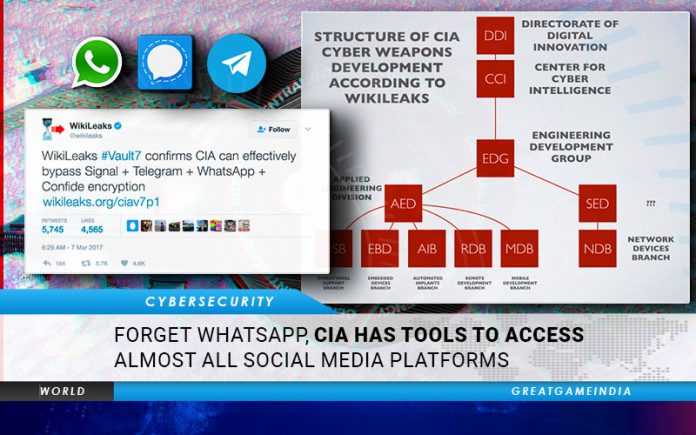
Recently, after WhatsApp updated its terms of use and privacy policy users have been migrating to other social media and messaging platforms due to concerns of their privacy. However, what is not being reported by media is that CIA has developed tools which can hack not just WhatsApp, but bypass the encryption of Signal, Telegram, Wiebo, Confide and Cloackman by hacking your smartphones itself.
On March 7th, 2017, Wikileaks released a giant file of 8,761 documents from the U.S. Central Intelligence Agency (CIA) codenamed Vault 7. Wikileaks called the leak the “first full part of the series “Year Zero”. The documents were stolen from a network that supposedly was “isolated” within the CIA itself.
The files include details on CIA’s software capabilities, such as the ability to compromise cars, smart TVs, web browsers and the operating systems of most smartphones, as well as other operating systems such as Microsoft Windows, macOS, and Linux. A CIA internal audit identified 91 malware tools out of more than 500 tools in use in 2016 being compromised by the release.
Your smart phone is your enemy. As is your smart TV, and computer OS, including, but obviously not limited to Linux. Understand this… anything… ANYTHING you say or do online can and will be intercepted, recorded, and used against you.



“Your smart phone is your enemy. As is your smart TV, and computer OS, including, but obviously not limited to Linux. Understand this… anything… ANYTHING you say or do online can and will be intercepted, recorded, and used against you.”
This needed to be said and everyone needs to understand this completely.
Also something to really understand, there are backdoors into every program and companies will gladly give the government the keys without question.
100% agree that nothing is safe, but just note that Signal/Telegram/etc are still better than plain text. The focus of the hacks for the article is on the end users device, not the service itself. Sure, maybe they have a central backdoor for that, but for these services that do end to end encryption based on end user keys, it’s very hard to decrypt all of these chains, especially if there’s no “master” keys.
In the article, they basically need to have hacked your phone, old school keylogger style, to snag input before it goes out. I’m guessing its installed via some malware or other whatnot, but this definitely isn’t as easy as downloading a bunch of plain text emails and searching them. It also makes it hard for them to just capture everything all the time. Also note keylogger-type malware only gets one side of the conversation. So if they aren’t able to hack Telegram/Signal/etc directly, they’d have to hack both sides of the conversation to get it all.
TLDR: Sure they can, but I don’t think they are en-masse. You don’t want too many of your “good” exploits deployed in the wild where people can find the problem and patch the holes. Also, there’s never going to be a fool-proof watch to patch the keylogger type holes. Something has to take non-encrypted data and encrypt it, and as long as you can always step into that process, then you’ll always have access, at least to one side of the conversation.
But best safe to assume you’re under a magnifying glass at all times.
I was having a conversation (him on his smart phone, me on my VOIP landline) with one of my brothers about a month ago when he mentioned something about “church”. Within about thirty seconds my VOIP “other line” beeped, his smart phone hadn’t beeped. I looked at the caller id screen on my phone to see who it was. The name was some church in South Carolina. I told my brother what I saw and he replied something to the effect of “how is that possible?” I told him “because they’re always listening, the phone companies and the government.” His response was a sarcastic “OK, Mr. Conspiracy Theorist”, his standard response when I tell him something that doesn’t agree with his Domonrat propaganda filled world view.
I have since sent him a few articles that I’ve come across in just casual reading of news and various other sites that I visit, since the conversation, about the phone companies and the government spying on phone calls, email, IM’s, Facefook and Twatter. I still haven’t be able to budge his cognitive dissonance. It probably won’t be budged until he’s on his way to some gulag and even then he’ll be in denial. In denial until the door on the cattle car slams shut. Then again, he’s been a good little Demonrat all of his life, unlike me, so maybe, just maybe, he’ll escape the ultimate solution.
I feel like “most” people won’t listen unless you links are CNN/MSNBC/BBC/etc. Any info from any other source is just “fake news”. Any other opinion is just “conspiracy”. I gave up trying to share anything anymore. I’m better off talking to the wind.