I originally posted this article on my Hidden Website accessible through the TOR network. This will be a tutorial on how to set up your own Hidden Service, accessible via TOR, either as a standalone website, or as a mirror to your “light web” site. Please understand that this article was written as a response to the profound censorship we are now experiencing on virtually every platform, and setting up your own “dark web” site allows you to circumvent being shut down by your web host, as has happened to a great many conservative sites, and keep your information up and online even if an unconstitutional entity seizes your domain name. This tutorial is intended for people to set up TOR sites, which use the .onion domain, for good and constructive purposes, as is not intended to help anyone engage in illegal activity. This is about preserving free speech during these very uncertain times. You can also see this article on the TOR Browser, and the easiest way to do this, rather than post the entire massively long url, is to go to https://tinyurl.com/hammersthor and navigate to the Communications tab. This link will not open in Firefox, but you can open it in either the TOR Browser, or by selecting (in Chrome, Brave or Dissenter Browser) SHIFT+ALT+N and pasting the link.
PART ONE
The party of tolerance has made it very clear that they intend to deplatform, censor and silence conservatives. If we don’t act proactively, eventually they will succeed. We believed that they would not take down President Trump with a stolen election, and they have. We believed that justice would be served, and that the deep state, and everything it represents, would finally, FINALLY pay for their crimes against the American people, face the music for their treachery, and be held accountable for their treason.
We believed it. Many Americans believed it. But evidently not enough. Now, those in power, along with those who have come back into power, will do everything possible to silence dissent. This is what communists do. This is what communism is.
So, you already know this. Everyone knows this. Now it is time to push forward with alternatives, since the kingmakers will not permit us to speak against them on their platforms. This is fine. In fact, this is actually excellent, because it removes the shackles of our own ignorance and allows us to learn how to circumvent their rule and live free. That is what we’re going to learn in this three-part series.
Your computer is a very powerful weapon of information against those who seek to silence us. Now it’s time to learn how to use it. This will be a tutorial on how to set up your own hidden-service website/blog, that cannot be taken down by your web host, because YOU are the web host. Your domain name cannot be seized by powerful government forces because it is not registered with ICANN. This is what is known as a dark web website, accessible through the TOR Browser network. Even tracing the signal to your computer will be very, very difficult, and you are going to keep a backup of it, to be installed elsewhere, in case they somehow do trace it back to your computer (remember, it is perfectly legal to set up a dark web website, you just should never use it for illegal activities). We will detail the steps to do this, and if you follow them correctly (don’t worry, it’s so easy a caveman can do it) you will have your website up in a matter of a couple of hours. Even if you’ve never built a web page before, you will be able to do this, and as you create it, refine it, and hone your skills, you will also be speaking your mind, sharing your ideas, and building a community of like-minded individuals working together, in a decentralized fashion, to bring the truth, and freedom, to everyone.
Protecting Your Computer
The first step is critical. This tutorial should be followed in the order presented. Some assumptions will be made, but no matter what kind of system you use, you should very easily be able to have your website up in short order. It is essential you have a notebook and pen to make some notes as you perform the steps, so you can easily repeat them when it is time to update your site, add new content, etc.
It is advisable to use a stationary, desktop computer for this purpose. No matter what kind of operating system, or OS you use, whether it is Windows, Mac or Linux, you should be connecting to the internet through a VPN. This is a bit of software that encrypts your internet signal and makes it difficult to impossible for either your ISP, or bad actors to intercept your internet traffic and see what you are doing online. This is especially important to protect your identity and your finances, but also to guard against spying on your activity. No doubt you have seen several VPN ads lately on TV, or listening to various podcasts. There are many companies to select from, and you might consider NordVPN and ProtonVPN. These are paid services, but generally quite affordable. Both NordVPN and ProtonVPN (a division of Protonmail) are hosted outside the United States, so they aren’t subject to the same disclosure laws as US-based VPN providers. This is one case (of very few) where “Made in America” is not better. Check out their websites, linked above, and subscribe to one of their services (or another based upon your research). Even if you never set up your own TOR website, you absolutely should encrypt your internet activity with a VPN in place. Even more important, be sure to set the “kill-switch” offered by these services, which will completely disable your internet connection in the event the VPN server goes down, thus keeping you protected… the reason for this is you may not know immediately if the server has gone down and your signal has reverted to your visible ip address.
Setting up a Virtual Machine
This step is not absolutely necessary, but strongly recommended, provided your computer has enough memory. Most computers have at least 4GB of RAM, but 8 would be better. This needs to be set up on a computer that you will leave on all the time, since you will want your TOR site up all the time.
A Virtual Machine can best be understood as a “computer within a computer”. In other words, say you are running Windows, or a Mac. The virtual machine will be a completely independent operating system that runs within your main computer, kind of like having two computers in one. For the purpose of this tutorial, your virtual machine will be specifically for running your TOR website, although it can serve many additional functions.
This author runs a virtual machine called Virtualbox. You can download the software for your operating system here and install it on your computer… it is free software and very stable. Install the software per the instructions for your specific system, then on to the next step.
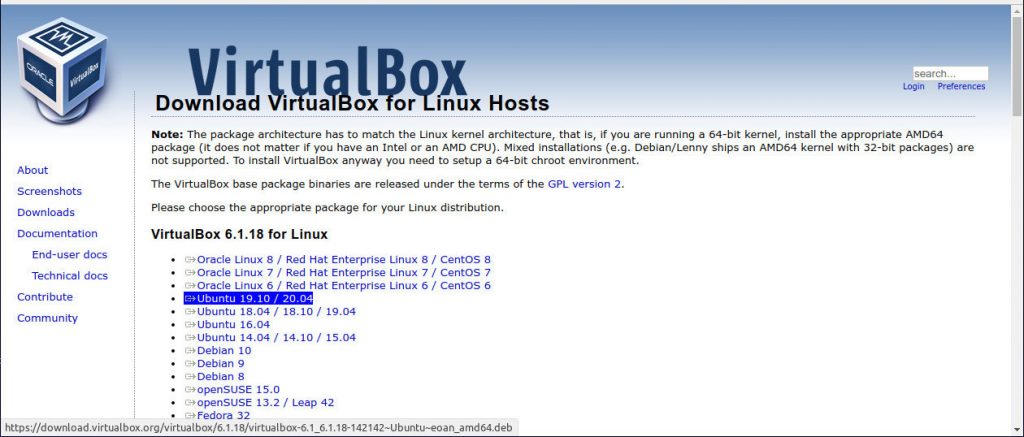
We’re going to install Linux Mint in Virtualbox. Linux Mint is a fabulous operating system that makes a wonderful replacement for Windows. It is free, and comes with some excellent (and free) programs already installed. Download the ISO file of Linux Mint here… it is a large file, and depending on your internet speed, can take from a few minutes to several hours to download. Save it to your Downloads folder, and go get a cup of coffee.
Now that you’ve downloaded the file, it’s time to install it in Virtualbox.
Stay Tuned for PART TWO. If you wish to see the entire article, it is available on our hidden website AT THIS LINK. Note… this link will not work in a normal browser. You will need to use the TOR Browser, or you can open it by using one of the following browsers, copying the link, and opening a New Private Window with TOR by selecting SHIFT+ALT+N: Brave Browser, Chromium, Chrome or the Dissenter Browser, which is supported by Gab.com. If you already currently use one of these browsers, try right-clicking on the link and selecting Open link in a private window with TOR.



+1 on “VM using VPN”. I am moving in this direction and will likely use a fresh VM each day, deleting and free space wiping the old VM, eliminating history files. One of the beauties of virtualization. But even this is only slightly more than a nuisance. What a statement about our government that we need to do this shit.
I appreciate this info very much. Might take a bit to figure it out, but look forward to learning. Thank you!
I am a hobby builder. From BSD to windows. I agree with everything here listed except one thing. I would cross off your list every single distro in the linux community that has moved to Systemd. every one. Linux Mint went systemd several years ago now.
I am on Devuan 3.0, they are a branch of debian team that bailed when systemd came to debian and they are on their 4th distro. I also am learning the basics around file formats in FreeBSD. I build windows boxes, everything but 10 theres no point to 10, its an OS as a service, its not really on your desktop thus not worth my time. doing an offline XP Pro Build right now on a toughbook Cf31.
there are only a handful of distros that are systemd free, FreeBSD being the most secure, and the hadrest to break into and anyone coming from windows is not going to do that. The least learning curve is going to be Devuan. Gentoo is high learning curve, Obarun is high learning curve, BSD of any varient is high learning curve, Absolute Linux is more user friendly for basic users that need nothing other than log in and get online, but if you aim to tinker that distro can be high learning curve based on slack i think, but you have to learn the window manager which on that one is IceWM.
If you are running a linux distro with systemd , there is no reasons whatso ever to take any privacy precautions, because you are being harvested from within before you ever even boot into the OS, systemd , networkd, has connected to the internet and in about a 2 minute period before you even see your desktop it has sent out all the information you have produced that it harvested the boot before. and there is nothing you can do about it. It is systemic. and it is a design, not a flaw of RedHat.
who are sell outs.
all other advice right on the money, switch out the Mint For a No Systemd distro and you are at the top of your game .
https://nosystemd.org/
@red So, your thoughts are very much appreciated, and there are a number of Linux users that object to Systemd for the same reasons. Having said that, and without turning this into a tech-blog, this is the reason for the suggestion in the tutorial to essentially “sandbox” (not a perfect analogy, but understandable for most) the OS in a Virtual Machine. Is it perfect? No, but it is significantly safer than NOT using a virtual machine. I also think it’s impossible to create a perfectly secure system (an oxymoron if I’ve ever heard one) with computer technology, in what will end up being a three-part series. This is a tutorial for the non-IT crowd, and a primer for those who would be interested in exploring the ideas.
I think it’s fair to suggest that it would be more secure than setting up a hidden service in a non-VM environment in Windows…
[…] Here is part two of the series. REVIEW PART ONE HERE […]
great article, look forward to more. A couple of questions, I had considered building a machine like a Rasberry Pi, there is a good write up over on Gab: https://gab.com/super_neet/posts/105726279189483773
however I have more laptops than i can shake a stick at. Do you have a minimum hdw recommendation in mind for builds as you describe instead of going VM on an existing machine? Don’t mind booting to USB for that matter as a VM but i question what level of machine would be best suited. All i have currently for such a project are small SSD’s, low RAM and i7 processors.
Any reflections will be appreciated. Thanks in advance.
@Ulfbehrt Great question. I think you could be very comfortable with anything with a 1.8 or faster processor, and 2gb of ram. 4 would be better, but the minimum requirements are less than that. I have a 15 year old laptop with 4gb and a Pentium processor that works just fine with a modest ssd. The biggest use is the Apache server, and even that is minimal. Also, as another poster indicated, you might consider a lighter distro that does not utilize systemd such as Devuan or MX Linux, which I have running on an even older laptop as a media server. You will literally be up and running in an hour if you dont have to go through setting up the VM. Just be sure you deploy a VPN with the kill-switch enabled.
Booting from a USB has the added benefit of having your hidden service available on whatever computer you wish… that is an excellent option. I would suggest encrypting the installation with either the laptop or if you deploy the installation on a USB for added security, in case an illegal entity gets their hands on your USB or your laptop. Damn difficult to break a good encryption at boot.
thanks so much, looking forward to giving it a go
[…] is Part Three, the final part in the series. PART ONE HERE, and PART TWO […]